Introduction
UN peacekeeping can evolve to become a learning enterprise that seeks out and applies new technologies and innovations on a continuous basis, thereby enabling it to be better prepared for the future.[1]
International peace and security remain at the heart of the United Nations (UN) since its foundation when nations committed to “save succeeding generations from the scourge of war.”[2] The UN Charter (Chapter VII) makes provisions for the Security Council to “decide what measures shall be taken in accordance with Articles 41 and 42 to maintain or restore international peace and security,” including regional Arrangements (Chapter VIII).[3] In this regard, the UN has often resorted to peace operations [4] (particularly peacekeeping) as one of the ‘tools’ to address threats to international peace and security.[5]
Since its first peacekeeping mission, the UN has deployed over 70 peacekeeping operations around the world.[6] Currently, the UN has 13 peacekeeping missions across Africa (7), Asia (1), Europe (2), and the Middle East (3) [7] (see Figure 1).
Regional and sub-regional organizations, as well as coalitions of States, have also been active in leading peace operations, particularly the North Atlantic Treaty Organization (NATO), the African Union (AU), the Organization for Security and Cooperation in Europe (OSCE), and the Economic Community of West African States (ECOWAS). Alongside multiple actors in peace operations are the rising complexities in both security and conflict dynamics (such as the increased use of Improvised Explosive Devices /IEDs/ by non-state armed groups), new threats (such as the ongoing COVID-19 pandemic) as well as shifts in political dynamics and contributions to peace operations. These and other disruptive changes demand resilience, agility, and adaptability by peace operations in order to effectively deliver on their mandates while upholding their legitimacy and credibility.
Figure 1: United Nations Peacekeeping Missions as of 31 March 2020.[8]
The world is also experiencing exponential growth in technologies and other forms of innovation from digital technologies, advanced robotics, artificial intelligence, blockchain, big data, Internet of Things (IoT), and 3D technologies, among others. In addition to the development of new technologies, their rates of diffusion, adoption, and application are also on the rise. On internet application, for instance, the International Telecommunications Union (ITU) estimates that 4.1 billion people (53.6 % of the global population) was using the Internet as of 2019, which was a significant rise from 2005’s 16.8% of the global population.[9] For digital technologies, by 2018, the subscription to mobile phones per 100 people of the global population was 106; in sub-Sahara Africa, the number stood at 82; the European Union at 123; the Middle East and North Africa at 106; East Asia and the Pacific at 122; and for fragile and conflict-affected States at 77.[10]
Technology portends significant benefits for the security and defense sectors. Leveraging new technologies remains crucial to enhance the resilience of peace operations by better addressing emerging security needs (such as the increasing IEDs and Vehicle-Borne Improvised Explosive Devices, VBIEDs) largely targeted at peacekeepers and civilians. New technologies can also play a significant role for both the Protection of Civilians (PoC) and force protection through enabling better observation, monitoring, surveillance and early-warning. New technologies are also becoming critical enablers and force multipliers in vast mission areas where intelligence generation, analysis and monitoring capabilities are increasingly in demand.
The Expert Panel on Technology and Innovation in UN Peacekeeping in its report ‘Performance Peacekeeping’ acknowledged that “UN peacekeeping remains well behind the curve” in technological adoption and application while noting that UN peacekeeping “can and must leapfrog into-at least-the current day and position itself to face the challenges of the future.” [11] Acknowledging the complexity of crises that peacekeepers are deployed to manage, the Report notes the essence of technology in peacekeeping and emphasizes that “no mission can be expected to succeed in today’s complex environments without an ability to innovate and make effective use of technology, and no advantage should be withheld from those working for the cause of peace.” [12]
As security challenges within areas where missions operate keep evolving, the adoption of new technologies will be key in building the resilience of peace operations. For peace operations, resilience also entails strategic anticipation and mapping the transforming nature of conflict, and ensuring that responses are agile and adaptable to these changes. The High-Level Independent Panel on Peace Operations (HIPPO) in its 2015 Report notes the necessity to adapt peace operations “to new circumstances” and the need to “ensure their increased effectiveness and appropriate use in future.” [13] A significant part of this change is enhancing the technological capabilities of peace operations to resonate with the present and future needs. For peace operations to enjoy legitimacy and credibility, they need to be adaptable and resilient to meet the evolving security needs of the populations they are mandated to serve and protect.
While new technologies are not a panacea in resolving all challenges peace operations face, they play a significant role in enabling peace operations reinvent themselves and implement their mandates in a more informed and effective manner amidst new challenges.
The Evolution of Peace Operations
Clearly we cannot continue to afford to work with 20th century tools in the 21st century.
– Hervé Ladsous [14]
Technology as a resilience factor for peace operations must be framed within the evolution of peace operations and the significant transformation of peace operations, as well as their future trajectories. A number of peace operations have complex and robust mandates and operate within challenging environments. The evolution of peace operations has also been shaped by the nature of security threats to global security, particularly the evolving nature of armed conflict.
Peace operations have transitioned from “Observer Missions,” whose principal responsibility was to observe activities and deployments of armed forces of conflicting states pegged on UN-mediated ceasefire agreements.[15] In its first forty years, UN peacekeeping was largely involved in the observation and supervision of ceasefires within interstate conflicts.[16]
“Interposed forces,” the “second generation” of peace operations, comprised of smaller units of soldiers conducting largely monitoring, observation and supervision functions being “interposed between conflicting armed forces.” [17] At times, these forces have to engage in physical separation of combatants to create conditions for monitoring of volatile areas and engage in efforts to ensure the adherence to ceasefires while ensuring parties do not gain new grounds.[18]
Multidimensional peace operations form the “third generation” of peacekeeping operations. Their role increased in the post-cold war era with the transformation of conflict to largely internal (intrastate) conflicts, rising in “both number and intensity,” and thereby more involvement of UN peace operations in states’ internal dynamics in the quest for sustainable peace and nation-building.[19] Since 1989, there have been more than 30 multidimensional peace operations.[20] Multidimensional peace operations comprise the majority of peace operations today. They are involved in a wider scope of functions including “disarmament, demobilization, and reintegration of former combatants,” humanitarian assistance, promotion and protection of human rights, restoration of the rule of law, facilitation of political processes, the protection of civilians,[21] intelligence, analysis, investigations, and forensics.
“Transitional administrations”—the “fourth generation” of peace operations established in the late 1990s—entailed the United Nations going beyond the supervision of peace agreements to exercising governance over entire territories over transitional periods.[22] Transitional peace operations are comprehensive and involve a wide scope of activities from education, military, legal, and even sanitation functions, bringing together civilian, police, and military actors.[23]
The post-1988 period has seen a shift in peace operations both quantitively and qualitatively, with 58 of the 71 UN peace operations established in that period.[24] Qualitatively, mandates assigned to peace operations became more complex, multidimensional, and entailed addressing some internal matters of States where they were deployed, largely monitoring aspects that are non-military by nature.[25]
In the 2000s, the Protection of Civilians (POC) mandate became central in UN peacekeeping, denoting an additional shift from state-building and peacebuilding mandates to “emergency humanitarian peacekeeping.” [26] Transformations within peace operations have also been defined by personnel contributors to peace operations with larger troop and police contributions from Africa and Asia.
Despite the evolution in peace operations, observation and the need for monitoring, mobility, and secure communication have been enduring. With the involvement of peace operations in volatile areas, functions such as information collection, analysis, peacekeeping intelligence, and engaging targets in hostile environments are gaining importance.
Technology as a Resilience Factor for Peace Operations
As the world’s technological revolution proceeds, the United Nations can benefit immensely from a plethora of technologies to assist its peace operations. Missing such opportunities means missing chances for peace …
– Walter Dorn [27]
Resilience for peace operations, while enabling missions to optimally respond to evolving security needs, is essential in upholding the credibility of the wider multilateral system. Peacekeeping “is the activity that the UN is most visibly associated with,” [28] hence adaptability and resilience for peace operations are linked to the credibility of the wider United Nations system. A number of factors are vital to enhancing the resilience of peace operations ranging from innovative systems of operations, partnerships, and the adoption of new technologies.
Peace operations have undergone a number of transformations and technology can/is already enhancing the resilience of peace operations amidst these transformations. In the future, more changes in peace operations are going to demand further adaptation for resilience. This section focusses on how technology can/is enhancing the resilience of peace operations amidst:
Dynamic security environments and changing conflict patterns (with a focus on the rising IED threat)
The increasing significance of the Protection of Civilians (POC) mandate.
Dynamic Security Environments and Changing Conflict Patterns
(with a Focus on the Rising IED Threat)
The period from the 1990s onwards has been characterized by increased deployment of peace operations, largely reflective of the rise in conflicts, most of them intrastate, protracted, and asymmetric in nature. There is also the frequent, intense, and indiscriminate use of IEDs, and this will be a defining threat for peace operations as IEDs are increasingly becoming the “weapons of choice” for non-state armed groups,[29] including in areas with peace operations deployed. This is the case for the United Nations Multidimensional Integrated Stabilization Mission in Mali (MINUSMA) and the African Union Mission in Somalia (AMISOM).
Belligerents, mostly without access to conventional armament, exploit the use of asymmetric tactics and weapons like IEDs to gain a tactical and operational advantage over peacekeepers, which often have led to high causalities among both peacekeepers and civilians.[30] While IED attacks are not pervasive across all missions, they are nevertheless drawing a significantly high number of peacekeeper casualties.[31] They also pose significant challenges to peacekeepers’ safety and mobility and restrict missions’ scope of operation.[32]
In Somalia, as is the case in Mali, the IED/VBIED attacks are increasingly compounded by mortar attacks, ambushes, raids, and attacks by rebels and terrorists on peacekeepers’ bases and convoys.[33] In Somalia, the terrorist group Al Shabab is also launching attacks using Under Vehicle Improvised Explosive Devices (UVIEDs), conducting ambushes and attacks along Main Supply Routes (MSRs) amidst a host of other asymmetric tactics, particularly suicide bombings and assassinations.[34]
There are projections that future missions might be deployed to environments facing similar threats, particularly to Syria, Yemen, and Libya.[35] Although missions are not entirely similar, an element of resilience for peace operations is drawing lessons from the experience of multinational forces in both Iraq and Afghanistan on technological applications to counter IEDs.
Both high-tech and low-tech solutions can be applied in counter-IED efforts. Relatively cheaper, tethered balloons, as well as blimps, may be used for surveillance purposes.[36] Mine-protected vehicles and armored ambulances,[37] as well as helicopters, enhance force protection and mobility within hostile missions and can also be used for medical evacuation. These are key to ensuring that forces are not exposed to harm.
The Expert Panel on Technology and Innovation in UN peacekeeping recommends that within areas affected by IEDs, convoys could be equipped with “small tactical UAVs” which could be used to generate “mobile intelligence,” while “surveillance and reconnaissance (ISR) platforms” could be used to survey chokepoints and other hazard spots along routes.[38] Electronic countermeasures (IED jammers) could be connected to intelligence resources to further mitigate the IED threat.[39] Smartphone applications to detect IEDs and other forms of Explosive Remnants of War (ERW) could be applied by missions in counter-IED efforts.[40] Ground Penetrating Radars (GPR) can be used to detect mines beneath the ground surface, while some hand-held devices can be used to detect explosive compositions.[41]
On identified hot spots, hazard points, or chokepoints, “tethered surveillance platforms” can be installed to improve surveillance.[42] Tethered aerostats can be integrated with devices such as acoustic detectors, radars, electro-optical/ infrared sensors, and high-resolution video cameras to enhance their surveillance capabilities.[43] They may also be linked to a ground control station for data transmission, media storage, and system management.[44] This is useful in transmitting information to peacekeepers stationed in various mission areas or peacekeepers on the move. Mine-protected vehicles are essential in protecting troops on the move and in offering evacuation platforms during emergencies.[45]
In countering devices that could potentially trigger IEDs, technology can be applied for both electrical and mechanical disruption.[46] While technology will enhance the resilience of peace operations in counter-IED efforts, working with local communities and mounting comprehensive global efforts to disrupt both networks and their enablers are essential elements in wider counter-IED efforts in peace operations.[47] Featuring technology in the trilateral counter-IED operational approaches is key, particularly in “preparing the force, defeating the device and attacking the network.” [48]
Developing inter-mission collaboration and partnerships on counter-IED technology application is key, particularly for missions facing similar challenges such as MINUSMA and AMISOM, and so is learning from NATO’s International Security Assistance Force (ISAF) experience in Afghanistan and Iraq. Sharing and continuous mentorship and learning will build the resilience of peace operations against emerging threats. It will also be key in monitoring patterns and understanding the changing technological dynamics of the IED threat.
Addressing varying technological capabilities and training among troop, police, and civilian contributors to peace operations remain vital in building technological resilience of the peace operations architecture in countering IEDs.
While technology and innovation are important in mitigating threats posed by IEDs, to ensure resilient counter-IED strategies, peace operations and national armies from which the troops are generated need to understand and cope with the evolving technological dimensions in the application of IEDs by belligerent actors. The continuing ease of spread of IED production and assemblage knowledge on the Internet remains a concern. The UN Secretary-General notes the alarming development of the use of Unmanned Aerial Vehicles (UAVs) to ‘air drop’ IEDs.[49] The Islamic State of Iraq and the Levant (ISIL) particularly has used “projected grenades” as “airborne improvised explosive devices.” [50] The disintegration of the group and its spread to other regions is a concern, specifically in regard to the spread of the technological know-how for the production and use of IEDs.
With the increasing need for better observation and monitoring capabilities for aerial reconnaissance, UAVs equipped with cameras are useful and the UN is applying UAVs since 2013 in missions in the Democratic Republic of Congo.[51] UAVs have also been deployed in Mali, where the Dutch contingent deployed UAVs and Apache helicopters equipped with camera pods for aerial reconnaissance.[52]
Aerostats equipped with cameras are useful in observation and monitoring and the UN is now using them in Mali in distant airfields where belligerents had previously launched attacks and also planted IEDs.[53] Aerostats could also be equipped with acoustic sensors and aid troops in identification of the direction of gunfire and further direct onboard cameras in that direction, thus providing early-warning, better situational awareness, and enhancing force protection.[54]
Non-State Armed Groups operating in some areas where missions are deployed are increasingly exploiting the cover of the dark for attacks on both civilians and peacekeepers [55] and for other nefarious purposes, including smuggling of human beings and illicit arms,[56] planting mines and other forms of explosives. Technology enables peacekeepers to “break the night barrier.” [57] Image intensifiers enhance visibility at night, while thermal infra-red (IR) sensors enable viewing at night heat from both human bodies and vehicles.[58] These capabilities, used with other technologies like drones with night-vision sensors, will continue enhancing the resilience of peace operations to operate both during the day and night as a conflict involving non-state actors continues to feature night tactical and operational elements. Advanced night vision goggles, as well as UAVs embedded with IR sensors, are key in enabling peacekeepers to conduct more effective night time operations.[59]
Emerging powers such as China and India are also playing an increasing role in peace operations both by contributing troops and funding peace operations. With the increased number of peace operations, this “new constellation” also has technological dynamics that can enhance their technological resilience. Missions can embrace more south-south technology cooperation as well as triangular technology cooperation whereby a technologically stronger country supports a Troop and Police Contributing Countries (TCC, PCC) through the organization leading the peace operation.[60]
The acquisition of technology is a crucial element and so is the training of peacekeepers on the application of technologies/innovations on sophisticated security issues like cybersecurity. There is a need for ongoing training (at the national level) and in the field during service to enhance peace operations’ resilience amidst the growing cybersecurity threats. There is also a need to address the challenge of the rotation of troops to ensure troops in the field bear the requisite technological capabilities for specific missions.
The Increasing Significance of the Protection of Civilians Mandate
This challenging mandate is often the yardstick by which the international community, and those whom we endeavour to protect, judge our worth as peacekeepers.[61]
Today, more than 95 % of peacekeepers are mandated to protect civilians.[62] Increasingly since the end of the Cold War, violent conflict has been largely intrastate in nature, involving non-state actors. These conflicts have triggered massive humanitarian crises, and civilians are increasingly deliberate targets. The rising attention to the protection of civilians is to ensure that the crises and failures to protect civilians by governments and peace operations in the 1990s across Rwanda, Bosnia, and Somalia are not repeated. By itself, the drive towards incorporating the protection of civilians in the mandates of most peace operations is in resonance with the evolving dynamics of contemporary conflicts, where civilians are targets or are increasingly caught in the crossfire, which points to the resilience of peace operations.[63]
The UN Secretary General in his report on the “Protection of Civilians in Armed Conflict” notes that in 2019 “more than 20,000 civilians had been killed or injured” in conflict-related attacks in 10 countries – “Afghanistan, the Central African Republic, Iraq, Libya, Nigeria, Somalia, South Sudan, Syrian Arab Republic, Ukraine, and Yemen.” [64] This number is certainly higher if the number of civilian casualties and civilians injured in Cameroon, Chad, the Democratic Republic of Congo, Mali, Mozambique, Myanmar, Niger, Sudan (Darfur), and the occupied Palestinian territory is factored in.[65]
With the majority of the peace operations bearing the mandate to protect civilians, their success in this function is contingent, among other factors, upon adequate resourcing and equipping. Bellamy, Williams, and Griffins note that “well-equipped operations” that are sent out with the support of the international community bear a greater likelihood of saving lives compared to “contentious, ill-equipped and ill-conceived operations.” [66]
In situations of armed conflict, timely and accurate information can save lives.[67] Digital technologies can be used in mission areas to assist civilians and peacekeepers to connect, share information and news, to conduct learning and also to take decisions.[68] This bolsters the element of “participatory peacekeeping,” where there is interaction between the mission and locals and the latter share information for early warning, thereby participating in enhancing their own security which also fosters “protection through connection.” [69]
The United Nations Stabilization Mission in DR Congo (MONUSCO) developed the “Community Alert Network,” which capitalized on the distribution of phones to leaders within the community who would then share information with the mission in the event of any looming danger.[70] Early-warning and intelligence will continue to be key in ensuring that peacekeepers act before actual incidents and thereby avert attacks before they happen. Technology will serve a key role in providing information on both planned incidents, sharing pictures, and with advanced Global Positioning Systems (GPS) enabled devices, sharing locations where civilians can be reached.
Satellite imagery can be accessed commercially, and peace operations can profit from an almost real-time reconnaissance with prices for the imagery falling along with latency periods and time of delivery.[71] Satellite imagery is useful in monitoring large distant areas, particularly where missions are mandated to protect civilians.
Missions can also use the Internet, SMS alert networks, television, radio, and social media to share information with civilians [72] as part of the technology for protection initiatives. In addition to SMS, technology-based Community Alert Networks (CANs) can use mobile phones, free hotline numbers, high-frequency (HF) radios, and satellite phones.[73] The use of technology for protection should be accompanied by safeguarding sensitive personal data to ensure that the privacy of vulnerable people under protection is adhered to.[74] There is a need to also watch out to ensure that belligerent actors do not exploit social media to spread disinformation, incite violence, and promote hatred, which entrenches divisiveness and exacerbates violence.[75]
Resilience will also ensure that missions continue to dedicate efforts towards social media monitoring, detection, and threat assessment as part of conflict mapping, considering that non-state armed groups and other belligerent groups are maliciously leveraging tools like social media for enticement, manipulation, recruitment and coordination.[76]
Since 2019, the Unite Aware (formerly referred to as the “Situational Awareness Programme”)—an IT applications platform—is being applied in peacekeeping missions for situational awareness.[77] The platform is comprised of applications such as the “Unite Aware Incidents” aiding the protection of civilians through tracking POC incidents and depositing them in a “central database repository,” the “Unite Aware Maps” which offer visual, geospatial mission data on both fixed and variables such as patrol plans as well as location of critical infrastructure and incidents, and the “Unite Aware Dashboards,” which offer customized views of data on POC issues such as number of rape incidents, killings and other incidents which can be further aggregated into specific locations, gender, and age.[78]
With the transformation of warfare and belligerents increasingly operating within communities both in urban and rural settings, empowering civilians with secure energy-saving communication technologies, particularly for areas without reliable electricity, is key for active engagement with the mission to communicate on any planned attacks and other nefarious activities being planned at the community level. This in turn, will enhance the security of both the civilians and the forces and enhance the resilience of peace operations amidst changing conflict dynamics. Photos taken by civilians can be used as evidence in legal proceedings addressing possible atrocities and violence against civilians.
UAVs used in mission areas equipped with capabilities such as thermal imaging cameras are crucial in capturing high-resolution and detailed imagery that is useful in locating objects, analyzing terrain, measuring distance and areas and, where there are incidents, UAVs can be used to obtain the exact location.[79] Noting the expansive terrain most missions cover, UAVs can play a crucial multiplier effect enabling the mission to “see and gather information” from locations that are either difficult or hostile to reach, thus enabling wider presence of the mission as well as advancing the protection of both civilians and the Force.[80] The information generated provides situational awareness, monitoring movements of violent armed groups as well as displaced civilian populations, and can be used later in the investigation of incidents related to the protection of civilians (POC).[81]
Technology will undoubtedly play a significant role in the protection of civilians. However, as peace operations harness technological opportunities as a resilience factor to enhance civilians’ protection, it is also important to plan for and address the gendered dynamics of technological divides, particularly on technological access and application. This will ensure peace operations are resilient in harnessing technology to protect all while “leaving no one behind.” In most of the societies where violent conflict is occurring, women are also culturally responsible for raising children and maintaining homesteads. Hence, the protection of children is largely tied to the protection of women. And if women do not have access to digital technologies and the Internet, which can be used in protection, that leaves children, and the elderly (for whom women are also carers) exposed and vulnerable.
Part of the foresight and resilience measures to ensure that the Internet can be used to communicate and enhance protection is planning on addressing the internet connectivity divide. Out of the current 13 UN-led peacekeeping operations, seven are in Africa, 3 in the Middle East, and 2 in Europe.[82] However, internet connectivity as of 2019 was 28.2 % in Africa, 51.6 % for the Arab States, 48.4 % for Asia and Pacific, and 82.5 % in Europe (Figure 2).[83]
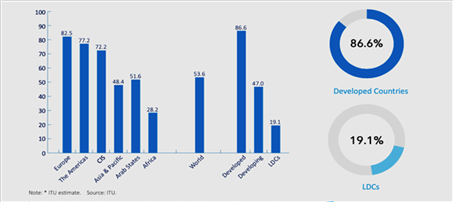
Figure 2: Percentage of Individuals using the Internet, by Region and Development Status, 2019.[84]
Future missions may need device mechanisms to lower cost and field appropriate internet connectivity for populations-at-risk if they are to tap into the Internet for protection. This is an aspect that will require more cooperation and partnership with the private sector.
Part of technological resilience will entail the protection of the minds in as much as peace operations focus on protecting the body. The battle for the minds of civilians is increasingly becoming one of the spaces contested by non-state armed groups who seek to influence civilians using the Internet and digital technologies. Protection of the minds will only gain greater importance amidst the great scope of protection. Strategic communication will become even more important; hence, in some missions such as Somalia, the UN is already engaging in strategic communication campaigns to counter the radicalizing messaging and effect from the Al Shabab terrorist group.[85]
Protection of civilians’ taping into digital technologies, particularly mobile phones, should factor in the adoption and use of mobile phones in the areas where peace operations are deployed. Mobile phones enable community members to alert peacekeepers of any danger (ongoing or impending) or even reporting on any irregular activities – this is, particularly, when belligerents are embedded within civilian populations. Part of resilience entails asking how these new threat dynamics can be mitigated and also how affordable mobile phones can be to the wider population for protection. While the subscription of mobile phones “per 100 people” stood at 106 in 2018, the numbers seem to be grim when it comes to conflict-affected countries, particularly those with active peace operations and most in need, as indicated in the next table.[86]
Table 1. Countries Experiencing Violent Conflict (All Apart from Yemen with Active Peace Operations) and Subscription of Mobile Phones per 100 People, 2018.
Country | Mobile phone subscription per 100 people |
| Afghanistan | 59 |
| Central African Republic | 27 |
| Democratic Republic of Congo | 43 |
| Mali | 115 |
| Somalia | 51 |
| South Sudan | 33 |
| Sudan | 72 |
| Yemen | 54 |
Technological adoption remains a significant step in bolstering the resilience of peace operations. Mapping and conducting strategic foresight are crucial for peace operations in order to anticipate, plan, and prepare for future threats. This is no small feat for peace operations that are constituted of forces from across the world with different military cultures, training, and capabilities. Incorporating strategic anticipation in peace operations is an important element to identify the tools, equipment, innovations, and technologies necessary to contribute to the resilience of peace operations.Conclusion
Cooperation and complementarity will continue to be important, noting the different capabilities of States within the international system and the contributions they can make to peace operations. Technological resilience for peace operations entails the resilience of the key actors in the peace operations, particularly the TCCs, PCCs, and increasingly the Technology Contributing Countries (TechCCs).[87] For the TechCCs, it is important to explore longer-term partnerships. The resilience of the militaries of the individual TCCs will largely impact the resilience of the wider peace operations architecture in relation to technology and innovation.
Peace operations are likely to be impacted by the dynamic changes and trends impacting the global security, political and economic spaces. Transformations in conflict are generating new needs and shifting the focus of mandates to non-traditional aspects such as stabilization amidst threats such as pandemics (as is the case currently with the ongoing COVID-19 pandemic) as well as adverse climate-change-related incidents such as flooding, droughts, and the attendant humanitarian needs they generate.
While the rapid development of technologies presents new opportunities for peace operations in implementing their mandates, technology adoption needs to consider potential unintended and undesired impacts associated with new technologies. Among these are dual-use technologies and the potential application of technologies for violent purposes, cyber intrusions into crucial mission data, and the hostile use of new technologies by belligerent actors.
Amidst changes that are ambiguous, uncertain, and complex,[88] while bearing very significant disruptions, peace operations will need to be agile, innovative, and adaptative to mitigate the threats while delivering on their mandates. Adopting technology and other innovations are opportunities for peace operations to navigate these changes more effectively.
Technology adoption must also be matched with agility and other resilience factors, among them strategic anticipation, foresight and innovation to adapt specific responses to mission needs as they emerge; the updating of manuals (such as the contingent owned equipment manual) to reflect the evolving needs for peace operations; continuous education and skills development for the end-users of the new technologies in mission areas; partnerships to strengthen the capabilities of the different personnel contributors; and continuous learning at the intra-mission level and inter-mission level on technology trends, mission needs and suitability.
Disclaimer
The views expressed are solely those of the author and do not represent official views of the PfP Consortium of Defense Academies and Security Studies Institutes, participating organizations, or the Consortium’s editors.
About the Author
Veronica Waeni Nzioki is a Foreign Service Officer in Kenya’s Ministry of Foreign Affairs and a researcher on peace and security. Her research interests focus on new technologies, innovation, peace operations, armed conflict, and warfare transformation. Veronica previously worked with the International Labor Organization (Employment Program) at the Central and Eastern Europe office in Budapest, Hungary. She also worked with the Jesuit Refugee Services in Northern Uganda, as well as the University of Nairobi as an academic programs coordinator and policy researcher. Veronica holds a Master of Advanced Studies in International and European Security jointly offered by the University of Geneva and the Geneva Centre for Security Policy (GCSP), Switzerland, a Master’s degree in International Relations from Corvinus University of Budapest, Hungary, and a Bachelor’s degree in Political Science and Sociology (Double Major) from the University of Nairobi, Kenya. She undertook Gender studies at the Abo Akademi University in Finland under the North-South-South Exchange Program. Veronica is a GCSP alumna under its Leadership in International Security Course (LISC).
E-mail: nziokiveronique@gmail.com
english.pdf.

